Last month, the FBI Cyber Division reported that, since COVID-19 hit and Shelter-in-Place (SIP) mandates took effect, the average number of cybersecurity complaints has risen to 4,000 complaints per day. That is astonishing compared to pre-COVID numbers, which average to around 1,000 complaints per day. There are several factors contributing to this spike in cyber breaches nationwide. The reality is that it all boils down to a lack of 360-degree cybersecurity plan for businesses, both large and small. But what does 360-degree protection look like?
Work from home culture has not necessarily created new methods in which bad actors attempt to steal information, but it has opened up new windows for them. With a large portion of the workforce working from the comfort of their own homes, it’s safe to say we are probably getting a bit lax on certain cybersecurity measures. But regardless of where we are working, we all need to be vigilant of cyber threats.
At work, we are mixing personal activities with business activities. You might have social media open in one window while some code scripting software is running in the next. Meanwhile, a toddler is waddling around behind you while a partner or roommate works from across the coffee table. There are so many more distractions than there used to be and cyber criminals know this. Bad actors know that the best means of slipping through the cracks in an otherwise airtight firewall is catching the human off-guard (or forcing a human error). However, with a cybersecurity plan this ca be prevented.
The Biggest Risk to Cybersecurity
The fact remains that, despite very skilled hackers and advanced malware programs, the largest threat to cybersecurity is phishing attacks. Verizon’s 2020 Data Breach Report shows that over 20% of successful cyber attacks are a result of phishing scams. A reminder that a phishing attack is when a bad actor assumes a fake trusted identity then reaches out in a message to dupe a recipient into clicking some link and/or otherwise taking some action (like providing requested information). The message could be an email, an IM, or a text message and all it takes for them to potentially steal your login credentials and any other information stored in your browser history, or drop a malware file that can do other nefarious things like install a key-logger (think everything you type is logged and sent to the bad guys) or other bad-intentioned software or tools.
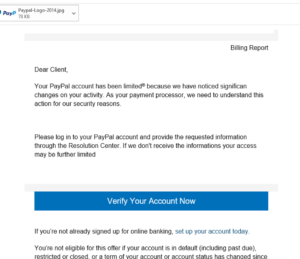
Phishing, smishing, and vishing are various forms and methods of social engineering. Social engineering is “the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.” Often, a phishing attack leverages an alarmist (ie. “Your account has been disabled or limited” or “unusual activity has been detected and…you need to provide your credentials to verify”) or ‘element of surprise’ (“you have won a MacBook!” or “Your Amazon order has shipped—click here to validate your information” ) tactics to solicit an emotional response; such as a faux distant family member pleading to the email recipient that they need to be wired money to get out of a tricky situation.
 .
. 
Cyber Criminals
The criminal may pose as a family member, an employer, a financial institution or, as we’ve seen in years past, some prince from a far-off nation. Another effective form of social engineering is for a bad actor to pose as a member of your company’s IT department and seek your login credentials to run some “system maintenance”. But common to the majority of these attacks, it is using surprise or fear-based tactics to get a response. Here are a couple of examples from my personal inbox!
Recently, someone messaged a Twitter employee asking for just that, claiming they were with Twitter’s IT team. And just like that, this bad actor was able to hack into Bill Gates’, Apple’s, Elon Musk’s, and Barack Obama’s Twitter accounts. Keep in mind that Twitter is a multibillion dollar company, spending millions of dollars on security software, applications, and cybersecurity experts. Despite these measures all it took was one employee slipping up with their log-in information to cause a full-blown meltdown and a very public scandal. A cybersecurity breach almost always boils down to human error.
Tightening Up Loose Ends
We can mitigate human error as best we can by training all of our employees, instead of relying on a single cybersecurity team or security software. A 360-degree cybersecurity plan means educating your workforce on the biggest cybersecurity threats in an ongoing manner and shifting the mindset of cybersecurity to “it is ALL of our responsibility” (people, process and technology). Cybersecurity technology and protections are good and important (think network or system firewalls, anti-malware and vulnerability scanning and management) but PEOPLE are the HUMAN FIREWALL and a cybersecurity plan would be beneficial.
Alongside leveraging basic security controls, tools and practices (like regularly applying patches/software and application updates) and employee training, companies can tighten up configurations for shared cloud storage applications like DropBox or Google Drive. At minimum, organizations should specify acceptable use of such solutions and where possible provide configuration guidance and oversight.
Another recent example of an inadvertent action that led to a lot of time, money and resources to determine if a breach or data loss had occurred: an HR professional at a very large enterprise software company uploaded a list of employees with personal identifying information, or PII, into a DropBox folder that didn’t have any access restrictions. As a result, this PII was potentially accessible to the entire organization, which is completely inappropriate and could have resulted in a large-scale information disclosure (2020 average is about $150.00 per individual record). Bottom line is everyone has to do their part to help secure our most sensitive data (be it corporate or personal).
Cybersecurity Best Practices
There is no catch all technical solution to effective cybersecurity and focusing on one solution can get you into trouble. If you’re only instructing employees to have strong passwords and change them often, or only educating them on common phishing scams or best practices for shared apps, then you will eventually have a cyber breach on your hands.
People have to have more direct responsibility for the data they create, the information they access and share, a level of awareness and vigilance relative to identifying potential threats and acting to mitigate AND having some basic knowledge of cybersecurity best practices (e.g. managing their credentials, using multi-factor authentication, applying OS and App security updates, changing default device admin passwords, using secure protocols, etc.,). Without being too grave, for many enterprises/businesses, it’s not a matter of if, it’s a matter of when. But all is not lost; together, there is much we can do to mitigate becoming a statistic.
You Can’t Silo Security
You can’t silo security, meaning you can’t rely on one person or one department to protect your organization. Every employee is a link in the cybersecurity chain, and all it takes is one weak link for a chain to snap. Companies with a cybersecurity plan will be the ones that have strong information security teams (across various business functions), effective security controls and solutions that include people-process-technology, comprehensive and ongoing cybersecurity training, and robust policy, standards and governance that can provide the appropriate security ‘guide rails’ and help to foster a culture of cybersecurity mindfulness and shared responsibility across an organization.
David Brezinski is Emtrain’s Cybersecurity Expert responsible for writing our Cybersecurity Training Course, as well as answering any questions that come in related to cybersecurity. David was recently a guest on Emtrain’s bi-weekly webcast #AlwaysLearning, hosted on LinkedIn Live. For a deeper dive into this topic, check out the recording here.










